
Burnt Orange Solutions Saskatoon IT Tip – Preventing Fileless Attacks
Our Saskatoon IT Tips are from the Trusted professionals at Burnt Orange Solutions. We promise to have a one-hour response time for all your Saskatoon IT support needs. Honesty and respect are important to us. In our latest IT Expert tip Article, we discuss preventing fileless attacks.
What Are Fileless Attacks?
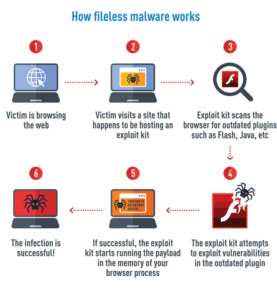 If we are interested in preventing fileless attacks, we need to understand what they are. The type of attacks people associate with “traditional” attacks by hackers involve malicious executable files. In other words, the hackers try and find some way for you to get & download their files onto your disk and run them to carry out their attack. Most traditional security software, the kind you might be familiar with, is designed to counteract this attack paradigm. This is done by scanning the files on your computer and removing any malicious files that are found.
If we are interested in preventing fileless attacks, we need to understand what they are. The type of attacks people associate with “traditional” attacks by hackers involve malicious executable files. In other words, the hackers try and find some way for you to get & download their files onto your disk and run them to carry out their attack. Most traditional security software, the kind you might be familiar with, is designed to counteract this attack paradigm. This is done by scanning the files on your computer and removing any malicious files that are found.
Fileless attacks use alternative approaches to gain access to your machine that does not involve loading malicious files.
Types of Fileless Attacks
- In-Memory – these attacks use code injection techniques to infest your short-term memory directly with malicious code. These attacks can run directly from memory without ever loading files onto your computer.
- Registry Attacks – Attackers can gain persistence on compromised machines by storing malicious scripts in the registry, helping the scripts survive system reboots.
- Piggy-Backing on Legitimate Programs – By abusing powerful legitimate system administration tools like PowerShell, Windows Management Instrumentation, PsExec, etc. that are built into Windows, attackers can carry out malicious activities without raising red flags.
Practical Steps for Preventing Fileless Attacks
- Practice the principle of least privilege – Ensure that user access and privileges are limited to the bare minimum they absolutely need.
- Patch Regularly – Patching programs is an important security consideration. Hackers take advantage of vulnerabilities in outdated program versions.
- Disable system admin tools you don’t use – First and foremost on the list is PowerShell. If disabling PowerShell isn’t a realistic option, consider using Constrained Language Mode to limit PowerShell to basic functionality, which makes many fileless attack techniques unusable.
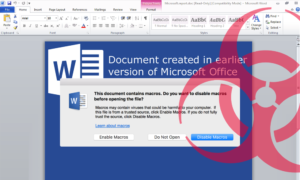
- Beware macros: Be extremely wary of Microsoft Office documents that prompt them to enable macros (or “enable content”), and utilize endpoint protection that blocks malicious macros before they can execute.
Want to Take Further Steps in Preventing Fileless Attacks?
We hope this article gave you some insight into preventing fileless attacks. If you believe you may have been a victim of an attack, or simply want to ensure your business’s IT security, contact the Trusted Saskatoon IT professionals at Burnt Orange Solutions and we can take IT worries off your plate.
Burnt Orange IT Solutions Products & Services:
- Managed Networks
- Backup and Recovery
- Data and Network Security
- Hosted Services
- Telephone Systems
- Secure WiFi Networks
“IT Support You Can Trust and Understand”
Burnt Orange Solutions are Trusted Saskatoon IT Experts
